How Clients Can Protect Themselves
Tips to Boost Your Cybersecurity

Establish Strong, Unique Passwords & Apply Effective Password Management

Routinely Review & Update Your Software to Ensure It Is the Most Current Version

Practice Caution & Verify Sources

Install Antivirus Software with a Firewall from a Reputable & Strongly Reviewed Vendor

Opt Into Two-factor Authentication

Consider Use of a VPN from a Reputable Vendor

Exercise Caution When Using Public Wi-Fi

Frequently Back Up Your Data

Be Prudent with the Information You Share Online

Regularly Monitor Your Accounts for Suspicious Activity & Properly Dispose of Sensitive Information

Be Alert for Social Engineering Scams

Never Use Unknown External Devices
Common Cyber Scams
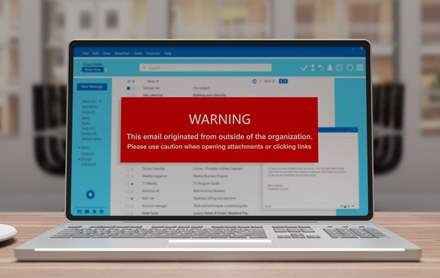
Phishing & Smishing Scams
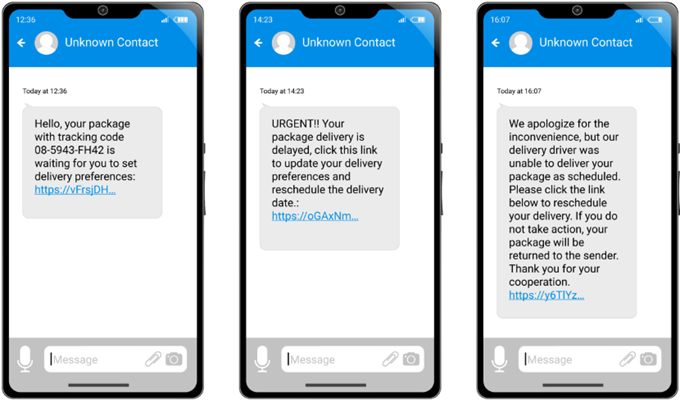
To Prevent Phishing / Smishing Scam Attacks:
Malware Attacks

To Prevent Malware Attacks:
Ransomware Attacks
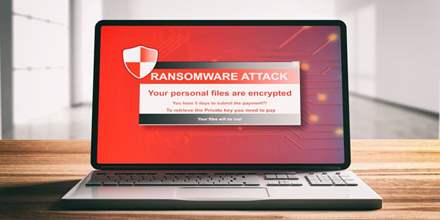
To Prevent Ransomware Attacks:

Identity Theft
To Prevent Identity Theft:
Sharing online
Freeze your credit & set alerts
Shred documents
Investment Scams

To Prevent Investment Scams:
Credit Card Fraud

To Prevent Credit Card Fraud:
Online Shopping Scams

To Prevent Online Shopping Scams:
Tech Support Scams

To Prevent Tech Support Scams:
Business Email Compromise (BEC) Scams

To Prevent BEC Scams:
Social Engineering Scams

To Prevent Social Engineering Scams:

Romance Scams
To Prevent Romance Scams:
Practice caution with unsolicited messages
Verify with research
Do not share sensitive information
Be alert for inconsistencies
Meet in person

Family Imposter Scams
To Prevent Family Imposter Scams:
Verify their identity
Evaluate the urgency
Communication channels
What to Do if You Are a Target of a Cyberattack

1. Contact legal authorities

2. Contact your financial institutions

3. Assess the situation

4. Identify the type of attack and pinpoint the instrument of attack

5. Isolate the exposed device
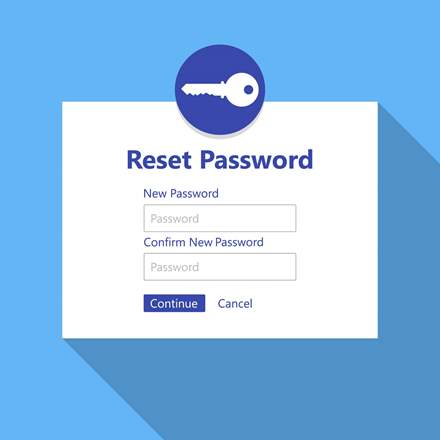
6. Create new passwords for your accounts

7. Review your accounts for unauthorized changes













